“`html
Microsoft Azure Shared Responsibility Model
Estimated reading time: 10 minutes
Key Takeaways
- Microsoft Azure shared responsibility model delineates security roles between Microsoft and customers.
- Understanding this model is crucial for effective cloud security management.
- Different service models (IaaS, PaaS, SaaS) have varying responsibility divisions.
- Implementing Azure security roles enhances security and compliance.
- Adhering to Microsoft cloud security best practices strengthens your security posture.
Table of Contents
- Introduction
- Understanding the Microsoft Azure Shared Responsibility Model
- Azure Security Roles
- Microsoft Cloud Security Best Practices
- Azure Security Compliance
- Azure Security Management
- Understanding Microsoft Shared Responsibility in Cloud
- Conclusion
- Additional Resources
- Frequently Asked Questions
Introduction
The Microsoft Azure shared responsibility model serves as the foundational concept for cloud security. Understanding this model is essential to effectively secure cloud environments. This blog post will delve into various aspects such as Azure security roles, Microsoft cloud security best practices, Azure security compliance, and Azure security management to provide a comprehensive understanding.
Understanding the Microsoft Azure Shared Responsibility Model
Definition:
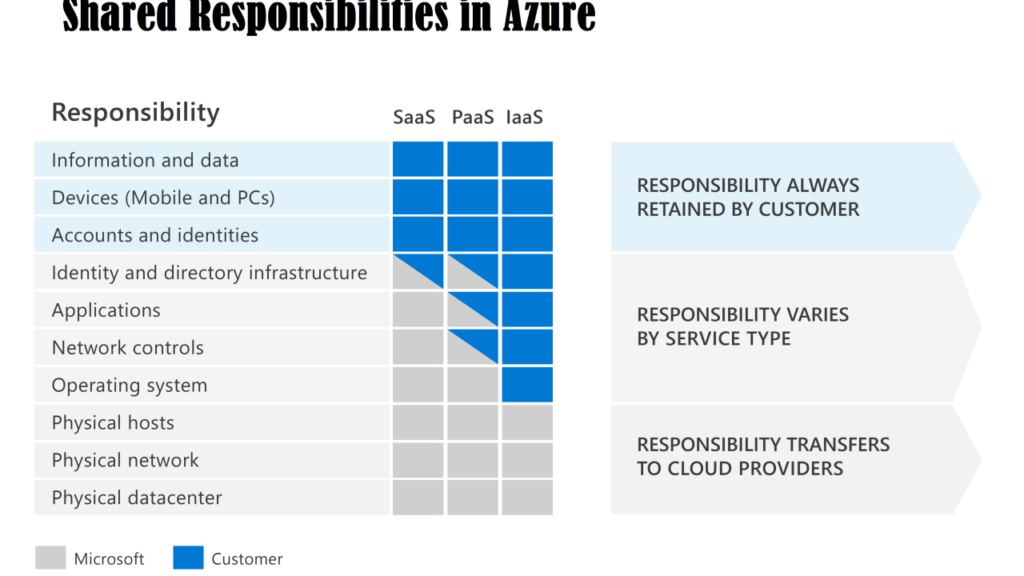
The Microsoft Azure shared responsibility model is a framework that delineates the security responsibilities between Microsoft and its customers. Microsoft is responsible for securing the underlying cloud infrastructure, known as the “security of the cloud,” which includes physical datacenters, networks, and host operating systems. (Source: Microsoft Documentation) Customers, on the other hand, are responsible for securing their data, identities, on-premises resources, and the cloud components they control, referred to as “security in the cloud.” These responsibilities vary based on the service model, such as IaaS, PaaS, or SaaS.
Division of Responsibilities:
The specific responsibilities of Microsoft versus the customer vary across different service models:
- IaaS: Microsoft manages the physical infrastructure, while customers manage the operating system, applications, and data.
- PaaS: Microsoft handles the infrastructure and platform, and customers manage applications and data.
- SaaS: Microsoft manages everything up to the application layer, and customers manage data and user access.
Significance:
This clear division is crucial for maintaining robust cloud security. Understanding these responsibilities helps organizations implement effective security measures, ensuring that both Microsoft and the customer maintain their respective roles in protecting the cloud environment.
Azure Security Roles
Overview:
Azure security roles are essential components for managing security within the shared responsibility framework. These roles help delegate specific security tasks, ensuring that responsibilities are clearly defined and managed.
Built-in Roles:
- Security Reader: Read-only access to security-related features in Azure. (Source: Azure Defender Permissions)
- Security Admin: Can update security policies and dismiss alerts in addition to read access. (Source: Azure Defender Permissions)
- Contributor: Full access to manage all resources but cannot assign roles. (Source: Role-Based Access Control)
- Owner: Full access, including the ability to assign roles. (Source: Role-Based Access Control)
Interaction within Shared Responsibility:
These roles help delegate specific security responsibilities, ensuring that individuals have the appropriate level of access to perform their duties. Role-based access control (RBAC) is vital in maintaining security and compliance by restricting access based on the principle of least privilege.
Examples:
For instance, administrators may utilize the Owner role to manage resources and assign roles, while security officers use the Security Admin role to update security policies and address alerts. Compliance managers might leverage the Security Reader role to audit security configurations without making changes.
Microsoft Cloud Security Best Practices
Alignment with Shared Responsibility:
Microsoft cloud security best practices support the shared responsibility model by providing guidelines and strategies that align with the defined security roles. These practices ensure that both Microsoft and customers effectively fulfill their responsibilities.
Best Practices Detailed:
- Implement Strong Identity and Access Management Policies:
- Use Azure Active Directory for managing user identities and access.
- Enable multi-factor authentication (MFA) to enhance security.
- Source: Research Findings Reference 18
- Encrypt Data Both in Transit and at Rest:
- Utilize Azure encryption services to protect data.
- Ensure encryption keys are securely managed.
- Source: Research Findings Reference 16
- Use Azure Security Center for Continuous Security Assessment and Management:
- Leverage Azure Security Center to monitor and manage security across resources.
- Source: Microsoft Press Store
- Regularly Update and Patch All Systems and Applications:
- Implement automated patch management to address vulnerabilities promptly.
- Source: Research Findings Reference 16
- Implement Network Security Controls, such as Firewalls and Network Segmentation:
- Use Azure Firewall and network security groups (NSGs) to control traffic.
- Segment networks to limit potential attack surfaces.
- Source: Research Findings Reference 16
Actionable Tips:
To implement these best practices:
- Configure Azure Active Directory settings to enforce strong authentication methods.
- Enable encryption features in Azure services and manage keys using Azure Key Vault.
- Set up Azure Security Center with continuous monitoring and automated threat detection.
- Schedule regular updates and leverage Azure Update Management for automated patching.
- Deploy Azure Firewall and define NSGs to enforce strict network policies.
Enhancing Security Posture:
Adhering to these best practices significantly strengthens the overall security framework, reducing vulnerabilities and enhancing the protection of cloud resources.
Azure Security Compliance
Compliance Requirements:
Azure security compliance involves meeting various regulatory and industry standards under the shared responsibility model. Microsoft manages compliance for the underlying infrastructure, while customers are responsible for compliance related to their applications and data configurations.
Compliance Certifications and Standards:
- ISO 27001: International standard for information security management. (Source: ISO 27001 Certification)
- HIPAA: Health Insurance Portability and Accountability Act compliance for protecting health information. (Source: HIPAA Compliance)
- PCI DSS: Payment Card Industry Data Security Standard for securing payment information. (Source: PCI DSS Compliance)
- SOC 1 and SOC 2: Service Organization Control reports for managing sensitive data. (Source: SOC Compliance)
Maintaining Compliance:
To maintain compliance, customers should configure Azure services in line with specific regulatory requirements. Utilizing tools like Azure Policy and Compliance Manager automates and monitors compliance, ensuring ongoing adherence to standards. (Source: Research Findings Reference 18)
Azure Security Management
Effective Strategies:
- Continuous Monitoring:
- Utilize Azure Monitor and Azure Security Center for real-time monitoring.
- Source: Research Findings Reference 19
- Implementing Azure Policy:
- Enforce organizational standards and compliance through policy definitions.
- Source: Azure Role-Based Access Control)
- Using Azure Sentinel for Advanced Threat Detection and Response:
- Deploy Azure Sentinel for proactive threat hunting and incident response.
- Source: Microsoft Press Store
- Regularly Reviewing and Updating Security Configurations:
- Schedule periodic audits and updates to security settings to address evolving threats.
- Source: Research Findings Reference 16
Tools and Services:
Azure-native tools like Azure Advisor and Azure Firewall assist in effective security management. These tools provide recommendations, enforce security policies, and protect against potential threats.
Importance of Continuous Monitoring and Incident Response:
Ongoing vigilance through continuous monitoring is essential for detecting and responding to security incidents promptly. Azure Sentinel enhances this capability by offering advanced threat detection and automated response mechanisms.
Understanding Microsoft Shared Responsibility in Cloud
Comprehensive Overview:
A thorough understanding of Microsoft shared responsibility in cloud environments is vital. This concept applies not only to Azure but also to all Microsoft cloud services, ensuring that security responsibilities are appropriately allocated and managed.
Comparison with Other Cloud Providers:
Compared to other major cloud providers like AWS and Google Cloud, Microsoft’s shared responsibility model shares similarities in the division of responsibilities but may differ in specific allocations. Understanding these differences helps organizations make informed decisions about their cloud security strategies.
Common Misconceptions:
A common misconception is that Microsoft handles all aspects of cloud security. In reality, while Microsoft secures the infrastructure, customers must actively manage and secure their data, applications, and user access to ensure comprehensive protection.
Customer Responsibilities:
Customers must actively configure and utilize Azure’s security tools to protect their data and applications. This includes implementing strong access controls, encrypting data, and regularly monitoring security settings. (Source: Research Findings Reference 16)
Conclusion
Recap of Key Points:
This blog post has explored the Microsoft Azure shared responsibility model, detailing the division of security responsibilities between Microsoft and customers. We covered Azure security roles, cloud security best practices, security compliance, and security management strategies.
Emphasis on Importance:
Understanding and adhering to the shared responsibility model is crucial for maintaining a secure cloud environment. It ensures that both Microsoft and customers are effectively contributing to cloud security.
Encouragement to Implement Best Practices and Tools:
Readers are encouraged to apply the discussed Microsoft cloud security best practices, utilize appropriate Azure security roles, and maintain Azure security compliance to enhance their security posture.
Final Thought:
Cloud security is a collaborative effort. With Microsoft handling foundational security, customers are responsible for protecting their data and applications, ensuring a secure and resilient cloud environment.
Additional Resources
- Official Microsoft Documentation: Microsoft Azure Shared Responsibility Model Documentation
- Further Reading on Azure Security Roles: Explore resources detailing Azure security roles and role-based access control.
- Best Practices and Compliance Guides: Access additional articles and guides on Microsoft cloud security best practices and Azure security compliance.
- Tools and Services: Utilize Azure tools such as Azure Security Center, Azure Sentinel, and Azure Policy to enhance security management.
Frequently Asked Questions
- Is cloud computing secure? Cloud providers implement strict security measures, but users must also follow best practices.
- What are the top cloud providers? The leading providers include AWS, Microsoft Azure, and Google Cloud.
- Can small businesses benefit from cloud computing? Yes! Cloud services offer affordable, scalable solutions for businesses of all sizes.
“`